Resilient communications is my passion. To the best of my ability, I conduct technology research and try to complement, document and popularly describe network technologies that can resist censorship - in the end, the truth is born in a dispute, and not behind the Iron Curtain. At the same time, the words “darknet” and “deep Internet” seem to me marginal and clickbait, because they poorly reflect the essence.
The idea for this article was born in a conversation with young system administrators who, in all seriousness, began to retell some fables about mysterious packages from the darknet, online torture chambers, Japanese evil spirits penetrating consciousness through the Tor network, and other trash content.
So, what are hidden networks and why the real state of affairs for an IT specialist is more fascinating than fairy tales from YouTube.
Action-packed tales
People tend to be afraid of the unknown, and some of us love the feeling of fear: that's why horror films, horror games and books with scary stories are created. In some cases, the unknown does not cause fear, but curiosity, which is most characteristic of the younger generation.
The search query “darknet” on YouTube gives almost a comprehensive answer about the nature of the origin of popular horror stories about the shadow Internet. What I like most is the whole epic of videos from various bloggers about packages from the darknet. Such videos were especially active five to two years ago (2016-2019), until the viewer got tired of such content. The most annoying thing is that there was nothing prohibited in the parcels. 
I honestly watched several of these videos in their entirety. This is clickbait in its purest form: promising shocking content, building up anticipation, and at the end of the forty-minute video, an airsoft gun and a piece of ground beef appear in the frame: keep vegans away from their screens!
One can imagine how, several centuries ago, young boys enthusiastically listened to fables from sailors who had the right to stories about the unknown. Today there are no blank spots left on the map of the Earth (except perhaps the bottom of the oceans) and almost any information can be quickly checked via the Internet.
However, the young man’s desire for accessible thrills has not gone away, so some viewers are happy to absorb stories about red rooms, where, allegedly, there is a live broadcast of violent actions, the outcome of which can be influenced by donating in cryptocurrency. 
Fortunately, a teenager's thrill does not come from inhuman violence, but only from the fantasy that it is possible, that there are scary places that you can chat about with friends.
Closer to reality
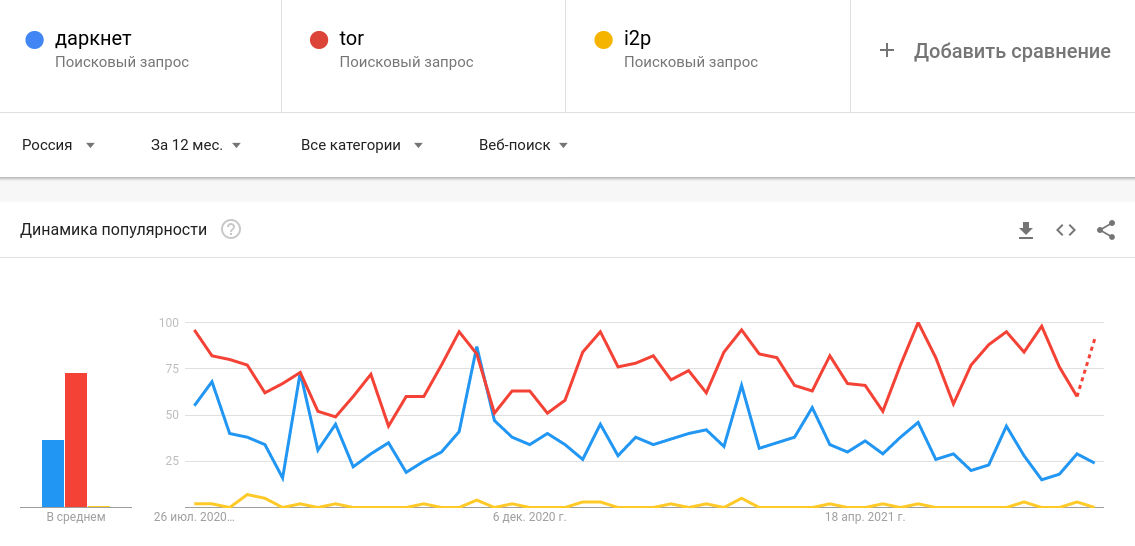
A quick analysis of search queries shows that the Tor network is almost the heart of the horror story generator. But (!), if an avid follower creepypastas from the Internet, if you bother to launch Tor Browser and try to find at least some of your stories, you will be very disappointed - the darknet is boring!
If you don't have an unhealthy interest in unhealthy things, half an hour of surfing onion sites will make you sad and that's all. No shocking content: some illegal substances, some taboo erotica and a couple of forums with people playing hackers, as well as an innumerable number of fraudulent sites that promise everything under the sun for an advance payment in cryptocurrency: from a smartphone to a gramophone. That's all.
"There are no red rooms on the darknet, let's leave!" - some disappointed lover of horror stories will say, but let him not rush to close the page. I published this article not to force obvious things, but with the goal of redirecting the energy of a young researcher into a creative direction. I am actively interested hidden networks, while I am not involved in criminal activities and am not looking for a fabulous prohibition. It seems to me that a short story about what fuels my interest may come in handy for anyone who is actively interested in the topic of fault-tolerant and hidden networks, or has ever heard of it.
Why does the darknet belong to an ordinary person?
Linking a number to accounts in various services has become the norm. On the one hand, this provides some level of protection against profile theft, but at the same time it is a direct identifier of the real identity that lies behind the fictitious name or nickname. It places restrictions on freedom of expression and is also a potential site for third-party invasions of privacy, from advertising analysis to political repression..
The jurisdiction of a site on a hidden network cannot be determined, so the laws there are of little application and everything is based on the internal agreements of the users themselves, which can also remain terra incognita. I can say with confidence that chats without registration, SMS, leaving your provider IDs and other traces are a pleasant place to relax with a relaxed atmosphere. Using hidden networks requires certain skills, so the community is usually a pleasant society of educated IT specialists - cozy chats and forums dedicated to software and networking. Somewhat reminiscent of the spirit of amateur radio many years ago, when people could communicate uncontrollably through the air, covering thousands of kilometers without regard to any restrictions.
Conventionally, yesterday Roskomnadzor blocked torrent trackers, today - the site FBK (banned organization in the Russian Federation), and tomorrow, perhaps, the sites of all religious organizations not related to the Russian Orthodox Church will be blocked. This list can be supplemented with thousands of past blockings and even more future ones can be assumed. A survey among my friends shows that most blocked web resources do not seem dangerous to them. If you check out register, You will undoubtedly find sites whose ban is completely justified from an ethical point of view: child pornography, drug sales, and the like. However, the fact that politically objectionable resources are blocked along with the websites of terrorist organizations causes outrage! I’ll say it again: drugs and illicit pornography can be found on the regular Internet, because it is impossible to block information instantly. If you don’t need this, you won’t be interested in such things in hidden networks.
An important advantage of hidden networks is the inability to block individual web resources. There are methods to paralyze the work of a particular hidden network as a whole, but the entire community is struggling with these kinds of difficulties, and not individual administrators of oppressed sites.
A logical continuation is censorship, or rather its absence in hidden networks. Is it worth putting up with the restriction of free thinking on the regular Internet, giving in to slogans about information hygiene? I think not. A child will learn about sex through any modern film or even a music video, inscriptions on the walls of neighboring houses will tell about drugs, a pedophile will watch schoolgirls in the yard... I try to approach this issue critically and reason like this: law enforcement agencies are needed, but not for not to imprison for likes and reposts, but to identify the real criminals. But how can you work on real criminals when you can prosecute any housewife or schoolchild for a slippery comment on VKontakte? It's half a day's work, but the stars are on the shoulder straps. Another thing is to infiltrate the criminal circle, collect evidence, and ultimately, with some degree of success, try to catch criminals who pose a real danger. Honestly, I am delighted with the foreign news about large-scale arrests and closures of large trading platforms that specialize in the sale of prohibited services, means and substances. This gives respect to the word "police". As for sanctions for liking an opposition public page: install wiretaps in all kitchens of the country and you will understand that there are not enough prisons for all violators.
If in the public consciousness hidden networks become a common tool like a web browser or instant messenger, the choice of security forces between a fifth-grader extremist and a drug dealer may finally tilt towards the real threat, because a year-long search for a schoolgirl followed by a fine is somehow not worth the promotion on duty, so all that remains is to do a real hunt for bad guys.
Freedom of speech, lack of censorship and everything like that are just part of the pie. For an average IT specialist, a seasoned geek or a novice computer student, the most delicious thing lies deeper - in the very implementation of hidden networks, because these are masterpieces of human thought: transmit information via the Internet, but with virtually no chance of determining the real location of the subscriber and without the ability to intercept his traffic via ways.
I am a beginner C++ programmer: I have several books and a couple of video courses under my belt. I gained a huge layer of practical skills and theoretical knowledge in the developer community i2pd. The enthusiasm for open source projects like this is completely different from the fanaticism for Apple and other proprietary hardware or software. These protocols are completely open, as is the source code of software clients: most often, the development of open source software for hidden networks is carried out with sheer enthusiasm to the best of each participant’s ability - these are very exciting projects and nice people! In commercial projects, participants live in the “Pay for life” paradigm - pay to live. Online programming courses from a popular Russian platform openly state that they set “horse” prices so as not to devalue knowledge. After what I saw - free knowledge in a cozy chat with a high level of communication - the slogans of commercial structures cause an ironic smile. I can’t imagine how many tens or hundreds of thousands of rubles it would take me to get an extensive knowledge base on cryptography in a year and a half from advertised courses. I’ll probably never know, because I got it for free: if you’re interested in cryptography, be sure to check out I2P, because it’s a cryptographic atlas: I’ve never seen such complex and varied cryptographic stuffing anywhere (Tor, for example, is much simpler). Of course, experienced developers with deformed consciousness strive to send them to study the source code in their naked form, but getting comments and explanations from the community is also in the order of things. No one hides knowledge, because people in the hidden network community have learned two things: by advising others, you grow yourself, and you also create human resources for future development and improvement of the technology. Those who do not understand this do not stay in the community.
The vast majority of modern online services are centralized: social networks, forums, etc. - an outsider can only be a consumer in them. The same partially applies to Internet providers. Hidden networks, unlike Vasya-Telecom LLC, do not have general directors, administrators, or any licensing restrictions on use. This means that each of us can not only use the technology, but also make our own contribution: from translating documentation into our native language to maintaining our own node, which complements the essence of the network on equal terms with others.
By the way, I don’t remember the last time I launched any online game, because the life of the community of hidden networks has become a second life for me, like an MMORPG for an avid gamer: I don’t know the participants personally, so their nicknames are perceived as familiar names game characters. Our “guild” always has a lot of grandiose plans and it’s wildly exciting to contribute as much as possible to them! And if you suddenly have an extra couple of rubles lying around, donations to the “game” are welcome: you can directly support the developers, or support your own network infrastructure (pay for server hosting and the like). To more clearly describe equality within the community, it can be noted that I, an unknown user and barely an admin, hosted the first starting node Yggdrasil in I2P. To do this, I had to solve a couple of small quests: write a script to generate a starting package with routers that have a Yggdrasil address, and also figure out how the resid (starting node) should function in general. When everything was done, I got real pleasure - Level up! To some, such entertainment may seem boring, but it is on such enthusiasm that the darknet exists and develops.
Hidden networks are not a place for horror stories, but a platform for free communication of people and personal development of any person who is not indifferent to network technologies and cryptography.
If the state is forced to resort to strict censorship, the problem is most likely not in the abundance of harmful information, but in the dead-end state structure.
The material reflects the subjective opinion of the author and is for entertainment purposes only..


